DeFi
Share
DeFi eliminates intermediaries by using smart contracts on blockchains to provide financial services like lending, borrowing, and trading. In 2026, the "DeFi 3.0" era is defined by Institutional DeFi and the integration of Real-World Assets (RWA). From liquidity provisioning on Uniswap to advanced lending on Aave, this tag tracks the evolution of autonomous financial systems, yield optimization, and the rise of AI-driven portfolio management in the decentralized economy.
67541 Articles
Created: 2026/02/02 18:52
Updated: 2026/02/02 18:52






Recommended by active authors
Latest Articles

Rails Launches Stellar Vaults for Crypto Derivatives
2026/02/04 11:42

Three dormant wallets, suspected to belong to the same entity, purchased 5,970 ETH eight hours ago.
2026/02/04 11:36
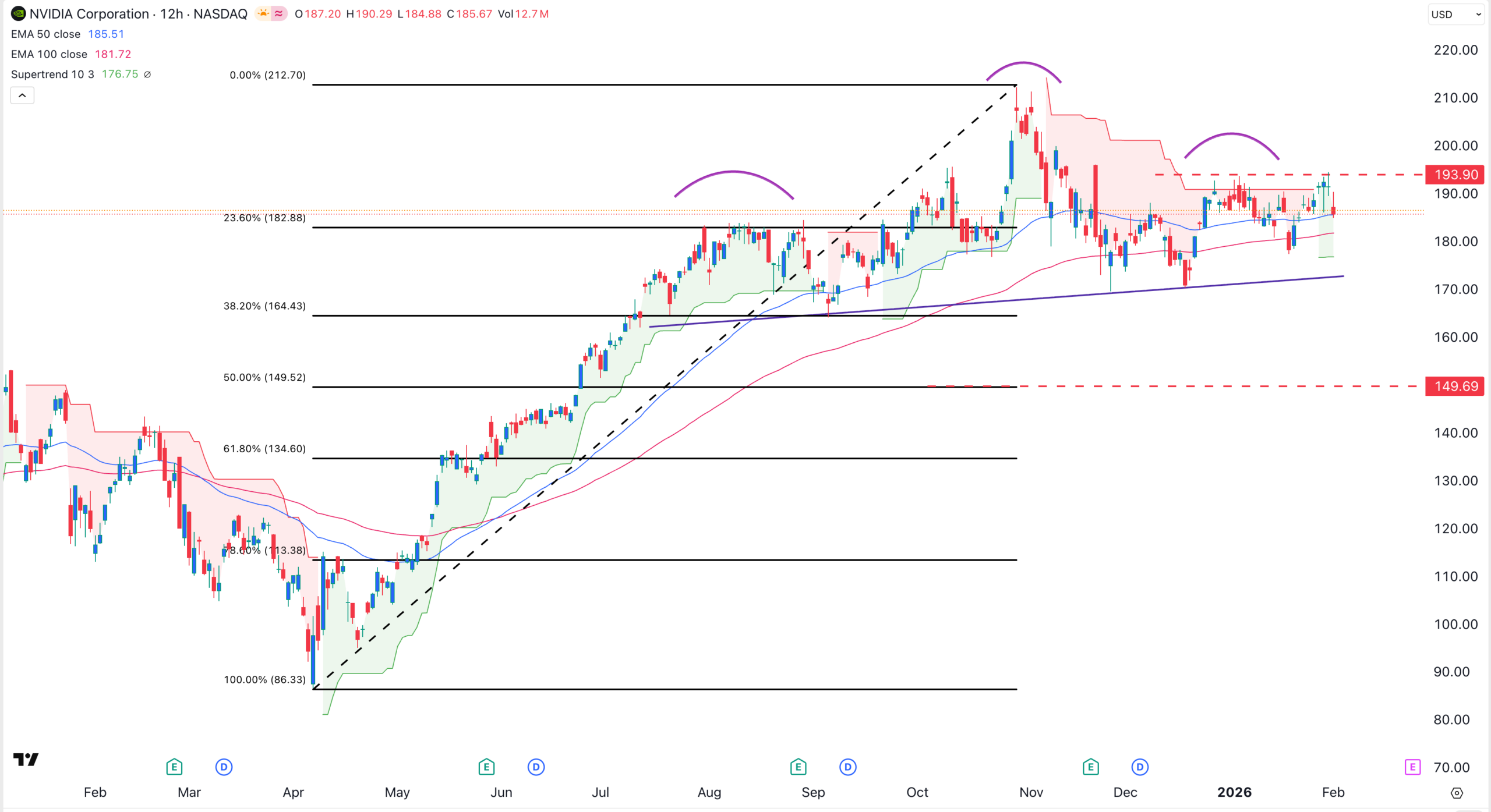
NVIDIA Stock Price Analysis as OpenAI Issues Concerns About its Chips
2026/02/04 11:27

The US Solana spot ETF saw a net inflow of $1.24 million in a single day.
2026/02/04 11:19

The US XRP spot ETF saw a net inflow of $19.46 million in a single day.
2026/02/04 11:17

